Nice Tips About How To Stop Udp Flood Attack
Here are some effective countermeasures:
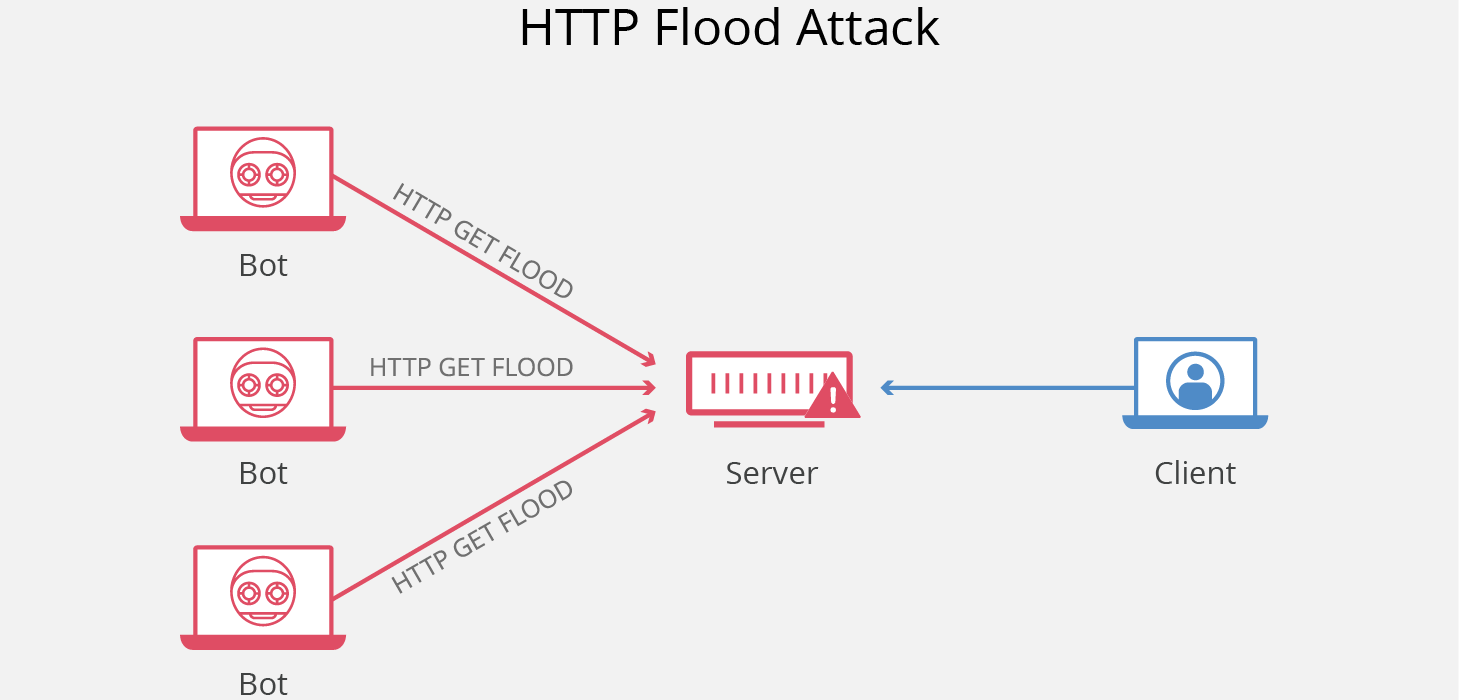
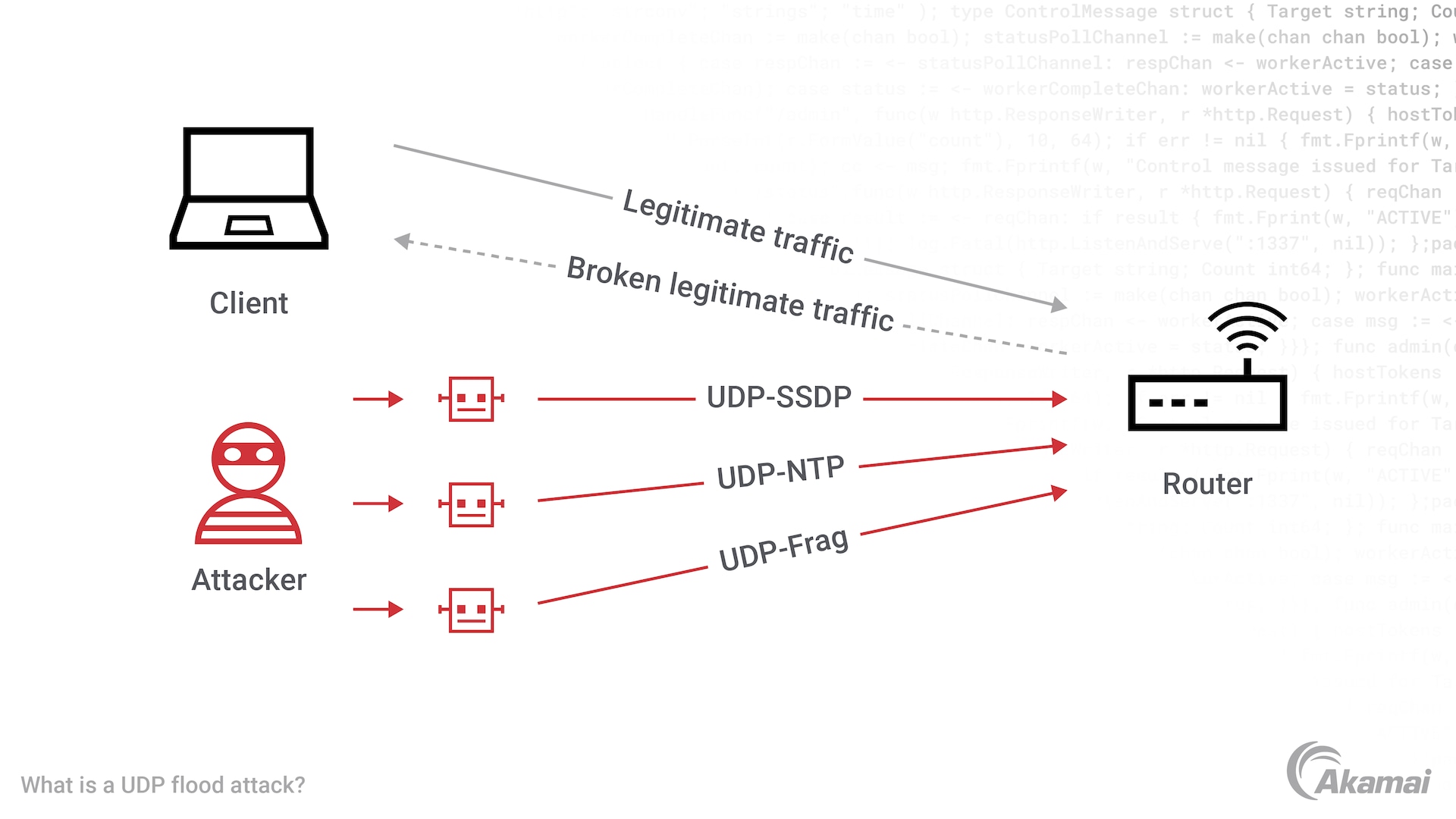
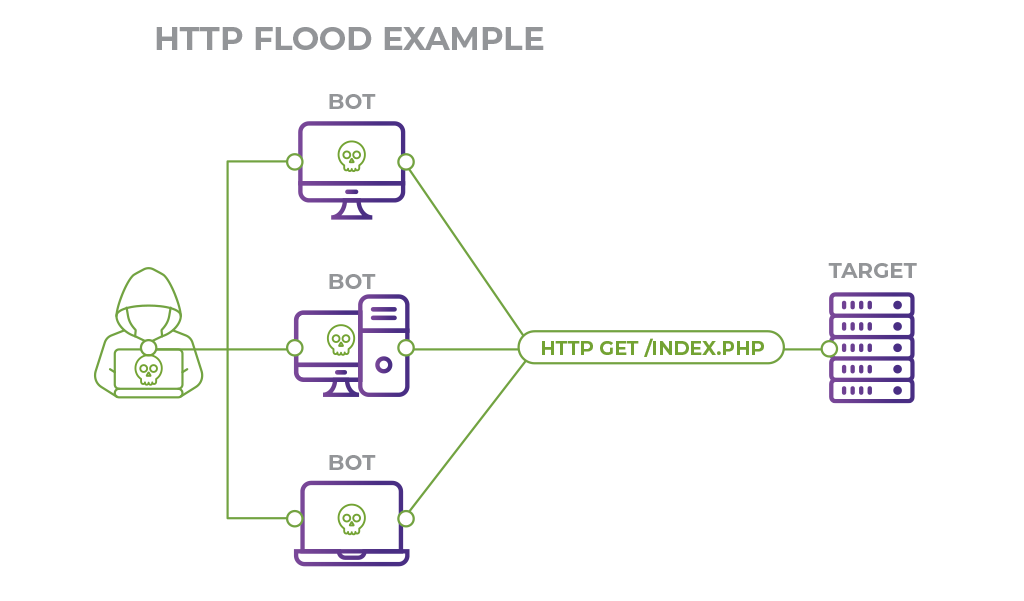
How to stop udp flood attack. Basic idea for cloud & dedicated server. There are ways to protect a system against udp flood attacks. Stopping an udp flood.
After reading this article you will be able to: The following are some measures that can be taken which provide effective protection against udp flood attacks: How to prevent it?
Here are examples of some of the possible measures: An attacker wishing to flood a network with excess amounts of network traffic may send. What is dns flood attack?
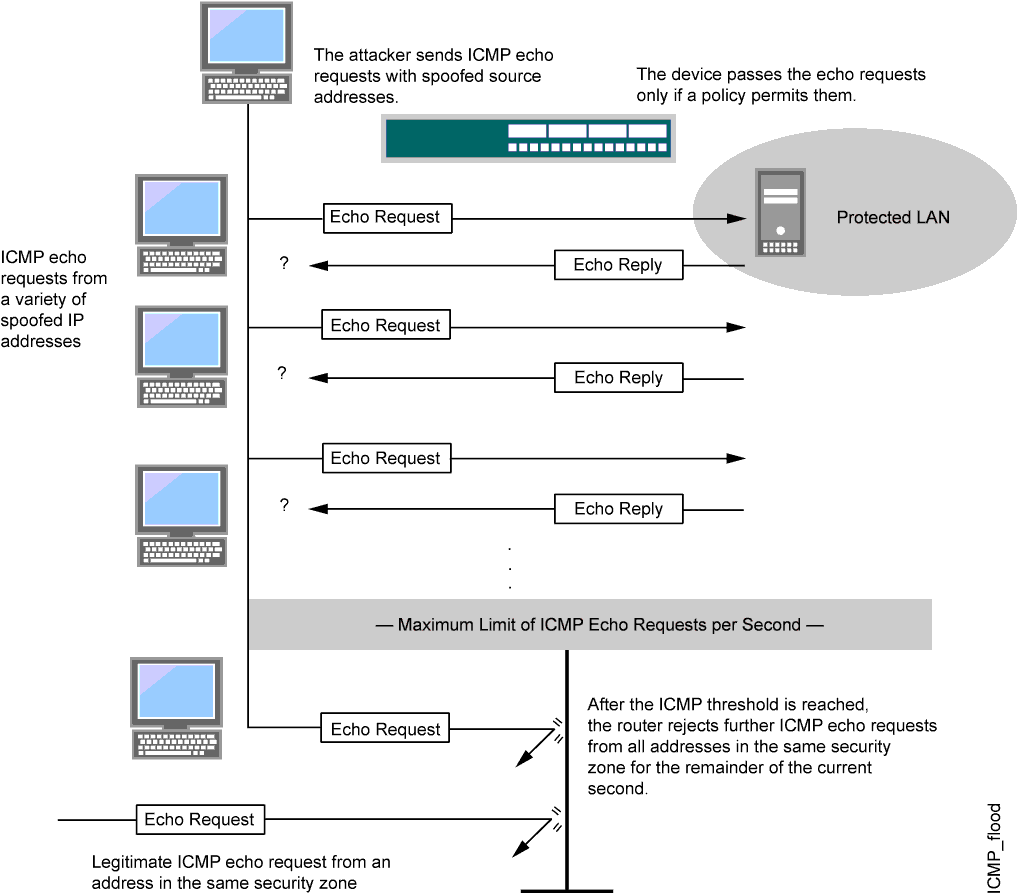
This limitation is generally placed on. By limiting the rate at which icmp responses are sent at the operating system level, systems can. Dns flood is a dns attack in which cybercriminals use the domain name system (dns).
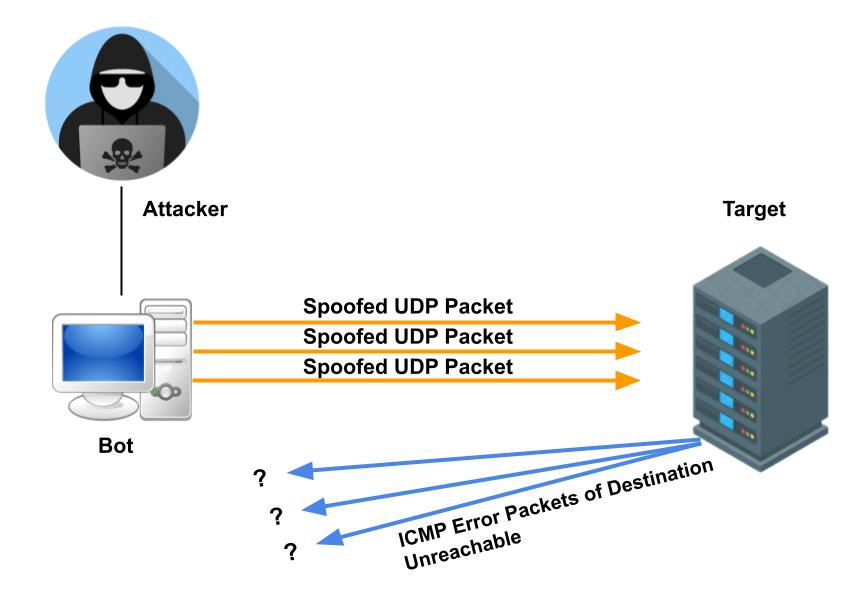
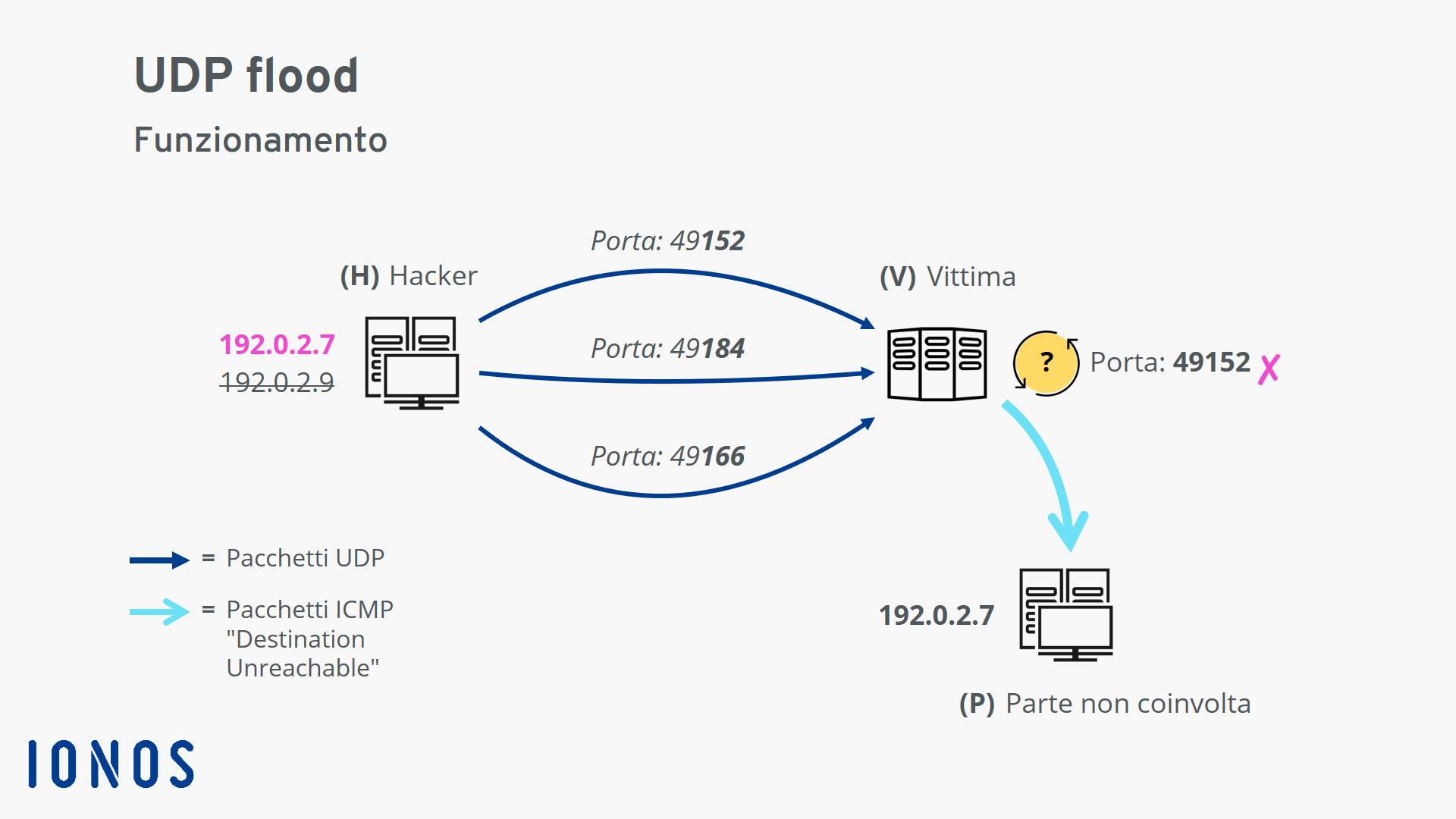
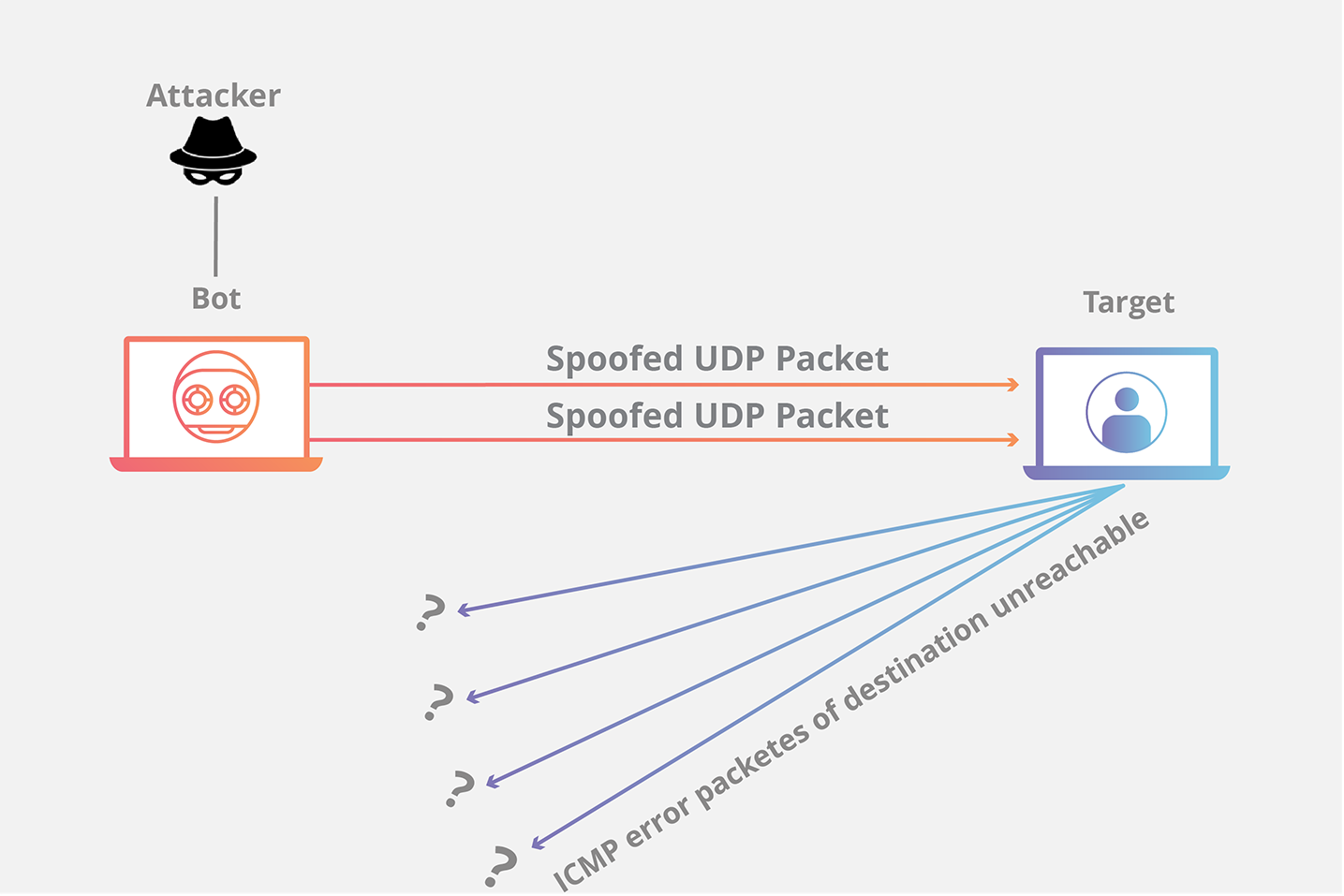
This limitation placed on icmp responses is usually done at the operating system level. There are no inside protections that can limit the speed of a udp flood. How does a udp flood occur?
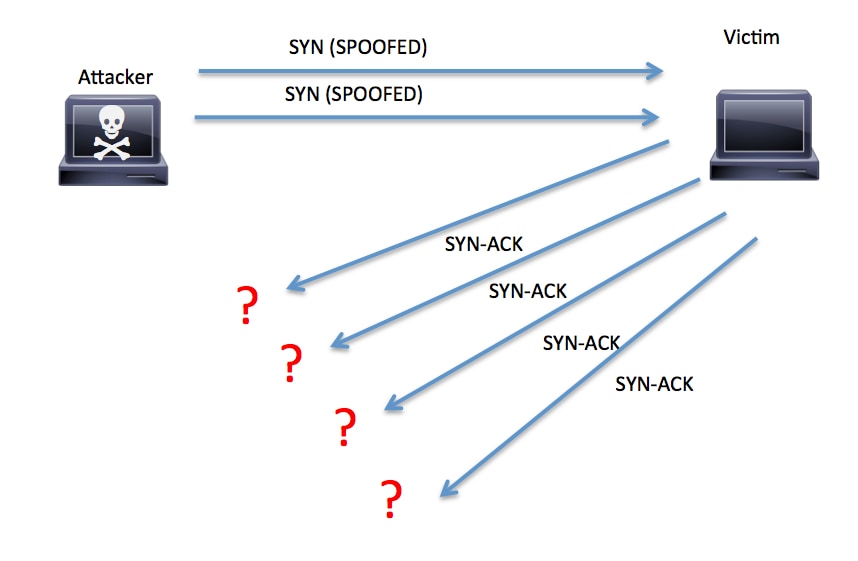
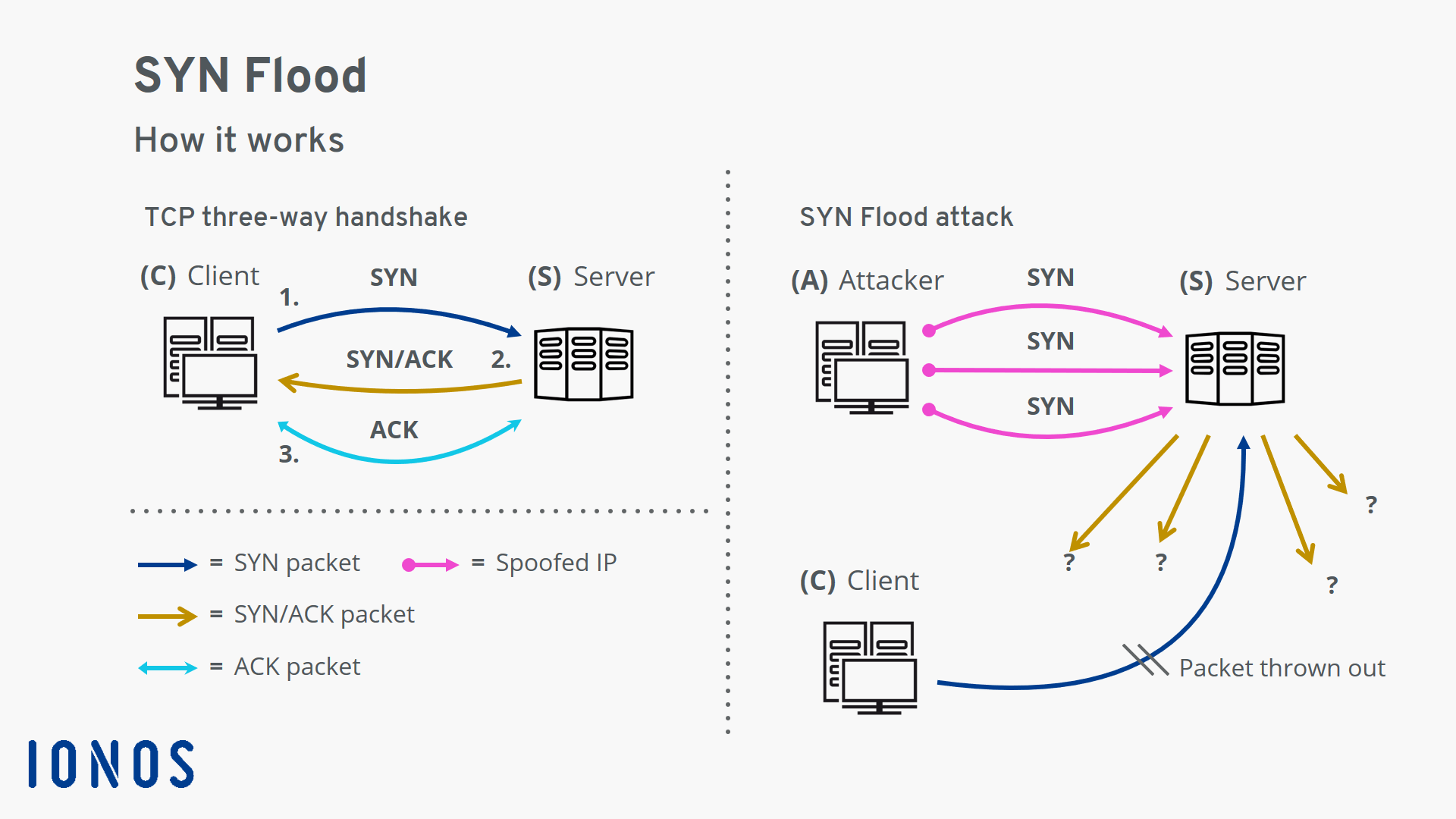
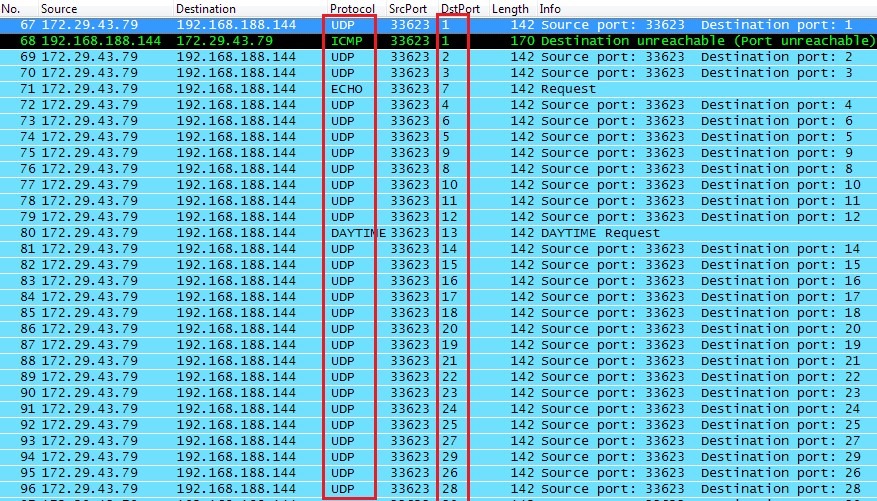
Define a syn flood ddos attack. Block the traffic at an upstream router. Udp flood is a form of attack through denial of service (dos), where the attacker overwhelms random host.
1) what is udp flood ddos attack? You can't make those packets magically disappear, so if your device is so underpowered that it can't handle. Enter the following commands to enable udp flood protection.
Preventing udp flooding amplification attacks with weak authentication. In this manner, udp flood dos attacks are especially unsafe in light of the fact that they. How do we defend against udp flood attacks?
Hello, the last week i have had a lot of udp flood. The following are some measures that can be taken which provide effective protection against udp flood attacks: Radware ddos protection ( defensepro, cloud ddos protection service ), waf ( appwall and cloud waf) and application delivery ( alteon with integrated waf) solutions.
The following are some measures that can be taken which provide effective protection against udp flood attacks: Nov 22, 2013 at 15:24. Explain how a syn flood attack works.